The advent of quantum computing is truly ushering in a new era of cybersecurity. In a few microseconds, these powerful new processors can solve encryption algorithms that would take hundreds years with current technology. Businesses must rethink their security architecture to ensure the continued security of their data.
Anticipating this need, IBM has leveraged its expertise in cryptography, quantum computing, and critical infrastructure to develop Quantum Safe.
This comprehensive range of tools, capabilities, and approaches allows businesses to gain a complete view of their encryption environment and take action to protect against delay attacks.
Key features of Quantum Safe technology
Each technological feature of Quantum Safe represents a step in the transition process. This provides the opportunity to explore, analyze, and reinvent cryptography.
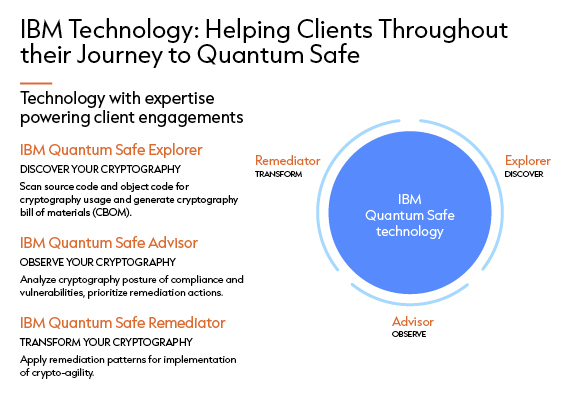
IBM Quantum Safe offers a suite of tools tailored for each phase of modernizing businesses managing and storing data.
Phase 1: Discovery
Before delving into a modernization project, it is crucial to understand your starting point. The first step is to identify all encrypted elements in your ecosystem. The second is to assess their interdependencies and build your Cryptography Bill of Materials (CBOM). This will guide all ensuing steps.
IBM Quantum Safe Explorer is the ideal tool for assisting companies during this phase. It scans your source code and objects to locate all encrypted artifacts and highlight their interdependencies. This information is catalogued in a knowledge base specifically structured to generate a CBOM.
Phase 2: Observation
Once all encrypted elements are identified, they must be analyzed to determine which are most critical for your company, ensuring compliance and conducting risk analyses. IBM Quantum Safe Advisor is perfectly suited to this task, managing your CBOM and probing your entire IT infrastructure to produce metadata to fuel your team’s analyses. Configurable to adhere to your internal policies, Advisor can greatly help you gain clarity on your compliance needs and prioritize modernization efforts.
Phase 3: Transformation
To assist you in this phase, IBM has created Quantum Safe Remediator, allowing you to test your encryption patterns and understand their impact on your systems. Easily integrable into your current security environment, Remediator allows you to choose between various encryption algorithms, certificates, and action key management services.
This enables you to stay agile and adapt quickly to threats and policy changes without significantly impacting your operations. Remediator also manages both Quantum Safe and traditional encryptions, facilitating a smooth transition without the need for multiple management tools. This allows you to adapt to the threats of today while preparing for those of tomorrow.
IBM’s lead and NOVIPRO’s expertise at your service
We have a few years before the quantum revolution fully takes hold, but the race to get there has already started.
A signal came through last July with the National Institute of Standards and Technology adopting the first algorithms resistant to quantum processors, which will become the industry standard. IBM leads the competition in this space, as three of the four algorithms selected for standardization are IBM-designed.
The advent of quantum computing poses a significant challenge for businesses. The transition is entirely achievable, and our team of NOVIPRO Security Advisors is here to help. As seasoned experts in IBM products, we are the ideal partner to guide you in implementing the Quantum Safe suite. Our Solution Architects can also help you identify the ideal solution and support the implementation process.
In summary, emerging quantum computing will make current encryption systems obsolete by the end of the decade. With a lead in the development of algorithms resistant to quantum processors, IBM and its partner, NOVIPRO, are well-positioned to guide businesses through the transition to quantum security.








