
NOVIPRO - Communauté zMeetup

Event - Chain Reaction

IT Trends 2025: Early Access Registration!

Webinar | Cloud: A New Paradigm and Sovereignty

Mainframe & Hybrid Cloud: The Winning Combination

Top Ways IBM watsonx Addresses Your AI Needs

Artificial Intelligence: An Essential Catalyst

How mainframe and cloud coexist for better cybersecurity
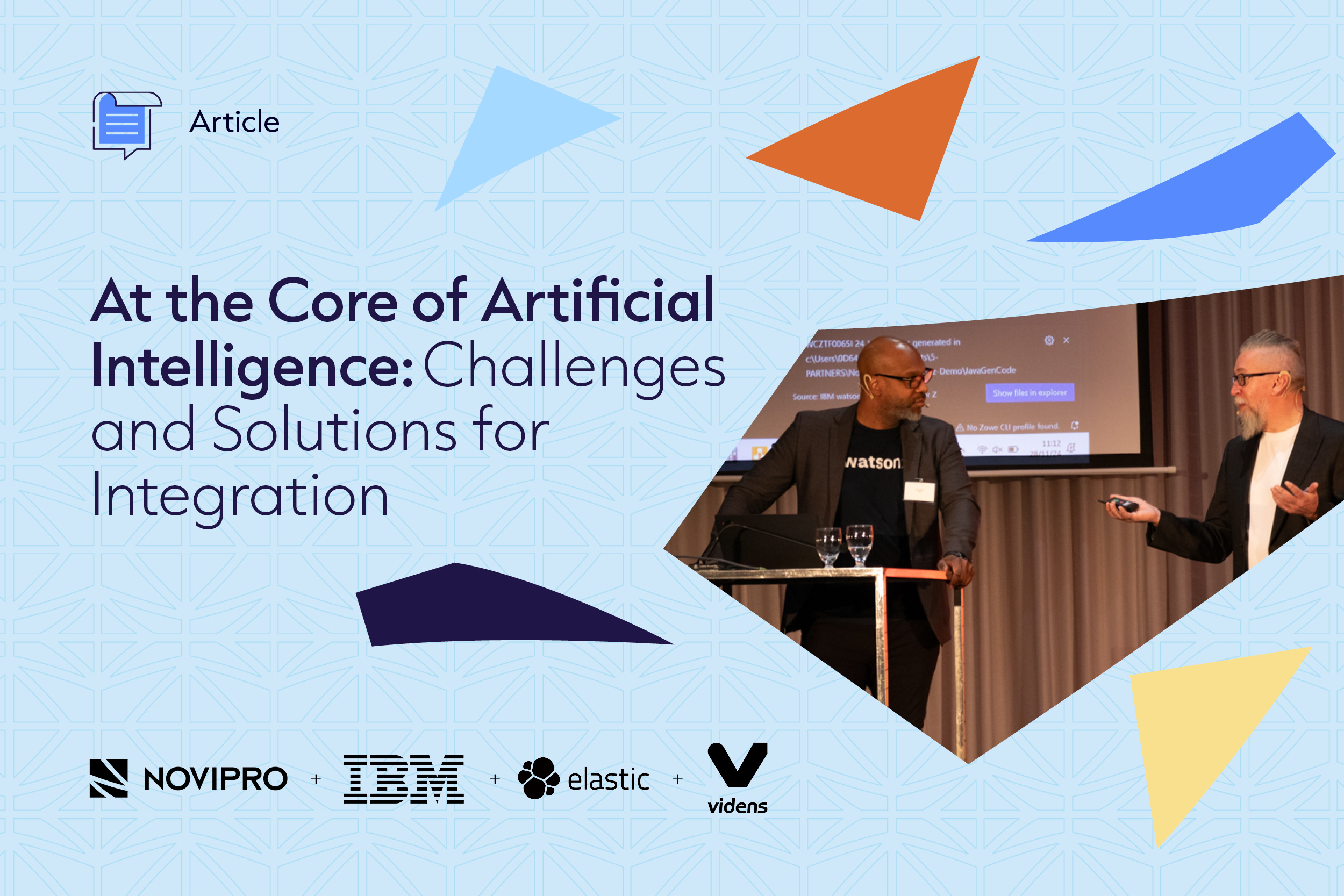
At the Core of AI: Challenges and Solutions for Integration

Why Every Business Needs to Be Ready for Cyber Threats

Modernization, The Key to Better Business Management

Cybersecurity Series - Strengthen your Security Posture Sustainably

Reducing Cyber Risk with Artificial Intelligence and Automation

Compliance with Law 25 and the Upcoming Bill C-27

How to Find the Right Cloud Partner for your IBM i System

NOVIPRO Announces Strategic Partnership with OVHcloud

CyberEX Underground: A Distinguished Fifth Edition

4 Essential Steps to Enhance the Robustness of your BCP

5 Myths about Cybersecurity

Secure your Data and Boost your Business Growth with AI

5 Reasons to Secure Your Spot at CyberEX 2024

4 Concerns about IBM® POWER® Systems

NOVIPRO: Our Future Journey Begins Now
IT Break - IT Trends 2024 : Advanced Data Analysis Edition
IT Break - IT Trends 2024 : Cybersecurity Edition

How to Achieve Modernization with a Focus on Security?

10 Questions to Help You in Your IT Hiring Process

Top 5 of Infor CSI’s New Features Unveiled at NOVIForum 2024

NOVIPRO's Third Decade: An Ambitious Renewal

Understanding the Impacts of VMware's Acquisition by Broadcom

Optimize Your Productivity with AI: NOVIPRO and IBM Expertise

How Olymel Enhances its Operational Efficiency with NOVIPRO and Blair

Best practices for integrating temporary IT resources into your team

2nd Life IT: Winners of NOVIPRO’s 1st Contest!

3 Good Reasons to Externalize your Backup System

Secure Your Network Communications Systems with NOVIPRO

The Latest IT Trends for Canadian Businesses

Need IT resources this summer? NOVIPRO is there for you!

The Second Decade of NOVIPRO: Consolidation of Success

Event - Hybrid Cloud by NOVIPRO

NOVIPRO Wins the Title of Best Sales of the Year

Bruno Guglielminetti's take on 2024 IT Trends

NOVIPRO Awarded Manufacturing Growth Partner of the Year by Infor

Webinar | Ready for AI ?
NOVIPRO Group Earns 2024 Great Place To Work® Certification

Celebrating NOVIPRO's 30th Anniversary

These 3 Steps Guarantee You an Excellent BCP

5 New Appointments at NOVIPRO Group

Exploring the Realities of AI in Customer Experience

Advanced Virtual Private Cloud Solution for IBM POWER® Systems

NOVIPRO's First Decade: the Foundations of Success

NOVIPRO Group Announces Relationship with Arrow Electronics

Protecting Your Operations Thanks to the Business Continuity Plan

IBM Quantum Safe: When Quantum Meets Security!

Optimize your server profitability with IBM Power Enterprise Pools 2.0

IBM Storage Fusion: Advantages of a Hybrid Cloud Platform

NOVIPRO Breaks Down Microsoft's 2 Recent Announcements

NOVIPRO Celebrates Its 30th Anniversary: A Remarkable Tech Journey

Webinar | Is your cloud architecture safe and robust enough ?

NOVIPRO Capital by NOVIPRO Group: Revolutionizing IT Financing

Webinar | IBM FlashSystem Experience: Cyber-Resilient to the core

Webinar | Ransomware Risk and Recovery

Webinar | Delve into the World of HPE GreenLake

NOVIPRO renews its SOC 2 Type II certification for its managed services
From Pause to Progress: Prioritizing Digital Transformation Journey

Webinar | Why Infor Cloud?

SAS as an effective and modern data insight platform by NOVIPRO

Webinar | Cloud Without Compromise
What’s new for Infor’s CloudSuite Industrial (SyteLine) ?

NOVIPRO achieves world's first IBM z16 system business partner sale

NOVIPRO becomes a « Champion » partner of Nutanix

Everything You Need to Know About Nutanix Multi-cloud Solutions

Webinar | Mining Your Own Data Like It's Gold
TrendMiner: A self-service industrial analytics tool

Quebec Law Bill 25: Does this concern me? 3 questions to ponder.

IT Break - Adopt an Innovative IT Infrastructure

NOVIPRO Group Acquires Blair Technology Solutions Inc.

A solid strategy for responding to cyberattacks

Cyberattacks: Are you ready to respond?

IT Break - Ransomware Recovery

Top 20 Private Cloud Questions Answered

The Dos and Dont's of Hybrid Cloud

PRESS RELEASE: Yves Paquette and Pierre Lanthier retire

IT Break - Endpoint Security

Webinar | Proactive Cybersecurity: Taking Charge of Your Security & Compliance Journey

Ransomware: 4 ways to protect and recover

7 tips to safeguard your company's data

Three Must-Haves for Ransomware Data Protection

IT Break - Ransomware Attack

Ransomware attacks: are you ready to fight?

Start 2022 right by educating your staff about cybersecurity

Cybersecurity: why not use an external resource?

Companies called upon to better protect personal data

Webinar | How Much are Insider Threats costing your company?

Resourcefulness to tackle the computer chips shortage

Quebec is looking to create a world-class innovation zone

Technological challenges and cyber attacks in 2022 | IT Portrait 2022

2022 Ponemon Cost of Insider Threats Global Report

Software asset management: a solution that pays!

IT Break - The ROI of Proactive Cybersecurity

IT Break - Effective Detection & Response By Connecting People, Process & Technology
IT Break - Cost of a Data Breach Report 2021 in Canada

Solutions that all IT experts should have in their toolbox

Application modernization: Full speed ahead!

Why modernize and unify your IT servers?

IT Break - Applying AI for Security: Separating Fact from Fiction

Webinar | Navigate Supply Chain Disruption: Using What-If Scenario Planning and Analytics

Microsoft’s Approach to Security

Evolved security management for our evolving businesses

Why COVID-19 has Accelerated Canadian Demand Digital Identity

Two-side of the PAM Coin & Securing all aspects of Privilege

Shifting the Security Analytics Paradigm: Cyber Threat Hunting and Response in a digitally transformed world

Secure your growth with zero trust: 3 stories for the new normal

Microsoft Defender for Identity (formerly Azure Advanced Threat Protection, also known as Azure ATP)

See Your Risks. Take Simple Steps to Stop Ransomware

Protecting Digital Identity: Continuously Securing Access

Data Security for Growth: A risk-based approach

Cybersecurity Operations Best Practices

5 Sure Fire Ways to Kill Security Awareness in Your Organization

A Tour of Saviynt Enterprise Identity Cloud (EIC)

The Top 10 Biggest and Boldest Insider Threat Incidents of 2020-2021

IT BREAK - DevSecOps
IT BREAK - API Security

Cloud Security Best Practices

IT Break - Password Pain

Securing the Future of Work in the Era of Ransomware, Insider Threats and Supply Chain Attacks

Change Your Perspective: View Your Network Like a Hacker

Shifting DAST Left

Cloud, DevOps, Security: Present & Future

Microsoft Azure Sentinel

IT Break - Proactive threat mitigation in production networks

Mapping your cloud migration strategy

Better, Faster Root Cause Analysis for the Food & Beverage Industry with TrendMiner Self-Service Analytics

IT Break - Backup and recovery through SaaS

Food & Beverage 4.0: Fitting the Pieces of the Process Puzzle Together

Webinar | Discover the benefits of migrating to SAS Viya

6 success factors in choosing an ERP

Keeping pace with a major application security trend: DevSecOps

IT Break -Production optimization through better visibility

IT Break - Mitigating Business Email Compromise

Infor Cloudsuite Distribution SXe Overview Videos

IT Break - Cloud App Security Broker

IT Break - Proofpoint Security Awareness Training

IT Break - Consumer IoT and privacy risks

IT Break - IBM X-Force Threat Intelligence Index

CPQ Returns $6.22 for Every Dollar Spent

The key to enterprise hybrid cloud strategy: An annual Forrester Consulting Study

How the Water & Wastewater Industry Can Use Self-Service Industrial Analytics to Improve Its Treatment Processes

IT Break - IRP : You've been hacked, and now what?

Advanced Process Analytics for Oil & Gas Upstream

Webinar | The State of IT in Canada - 2020: The Year of Upheaval

The Year When Everything Changed

Webinar | How to improve your production with TrendMiner?
Secure Remote Workers

Advanced threats call for Advanced Malware Protection

Five tips to enable a remote workforce securely

Big Security in a Small Business World

IT Consumption

IT Break - 2021 IT Trends

2021 IT portrait of Canadian medium and large sized companies

IT Break - Network Monitoring: Shift from a reactive to proactive organization

Migrate to peace of mind with NOVIPRO

Optimize your business processes with IoT and advanced analytics

Cloud computing is the answer to rising risks

The cloud and information security: What’s the relationship?

Personal data protection: a new imperative that’s here to stay

Cybersecurity Investments Held Back by the COVID-19 Pandemic

Cybersecurity: How to keep threats at bay?

Cybersecurity: a strategic investment

From office to work-from-home via the cloud

Disaster recovery and the cloud

Company knocked out by cyberattack

IBM Story | Cyber wars

IT Break - Zero Trust

Access control | A Ransomware Story: What happened, the response and the way forward

Access control | 6 Keys to Risk-based Assurance for the Remote Workforce and Security Operations

Visibility | Capture the Cloud with SASE

Visibility | Hunting for threats in a hybrid, multicloud world

Detection and response | Practical Threat Hunting: Straight Facts and Substantial Impacts

Access control | Measuring Risk in 2020-Enterprise of Things Report

Visibility | Don’t Wait for the Breach: Perfecting Your Splunk Alerts

Detection and response | Cyber Resilience: Reaching the New Frontier in DevSecOps

Visibility | Tools, Techniques, and Business case of hunting the Advanced Persistent Threat

Visibility | Respond faster with better data by using a Packetbroker to clear the noise

Data protection | 4 Steps to Reducing insider risk in the new [work] reality

Data protection | IBM Digital Trust – protecting what matters
Access control | Secure Remote Worker

Cybersecurity 20/20 | Introduction

A Pragmatic View of Implementing Zero Trust

Cybersecurity in the new normal

Digital Identity - A Driver for Canadian Inclusion and Prosperity
A day in the life of a Buyer

A day in the life of a Customer Service User

IT Break - Emerging stronger in the new normal

Artificial intelligence and machine learning in your organization

Key considerations for implementing secure telework at scale

7 critical considerations for firewall performance in the era of secure remote work

Top security concerns stemming from digital innovation

Text Analytics for Executives


